What Is I2P & How Does It Compare vs. Tor Browser?
The I2P (Invisible Internet Project) is an anonymous communication system within the public Internet (a.k.a. the Clearnet). It is a peer-to-peer communications network that takes advantage of the Internet infrastructure but uses end-to-end encryption and other techniques to make its users anonymous.
I2P Review – Is it a good alternative to Tor and VPNs?
In this article, we’ll look at how I2P works, and compare it to two other online privacy tools: Tor, and VPNs. Then we’ll look at how you can get connected to I2P and start taking advantage of the anonymity it offers.
If you would prefer a video introduction to I2P, this March 15th, 2018 presentation by Aaron Jones runs an hour and a half and goes into great detail.
Who develops / manages I2P?
As befits an anonymous messaging system, the people who develop and manage I2P are mostly anonymous themselves. Here is a partial list of the project team as of December 2018:
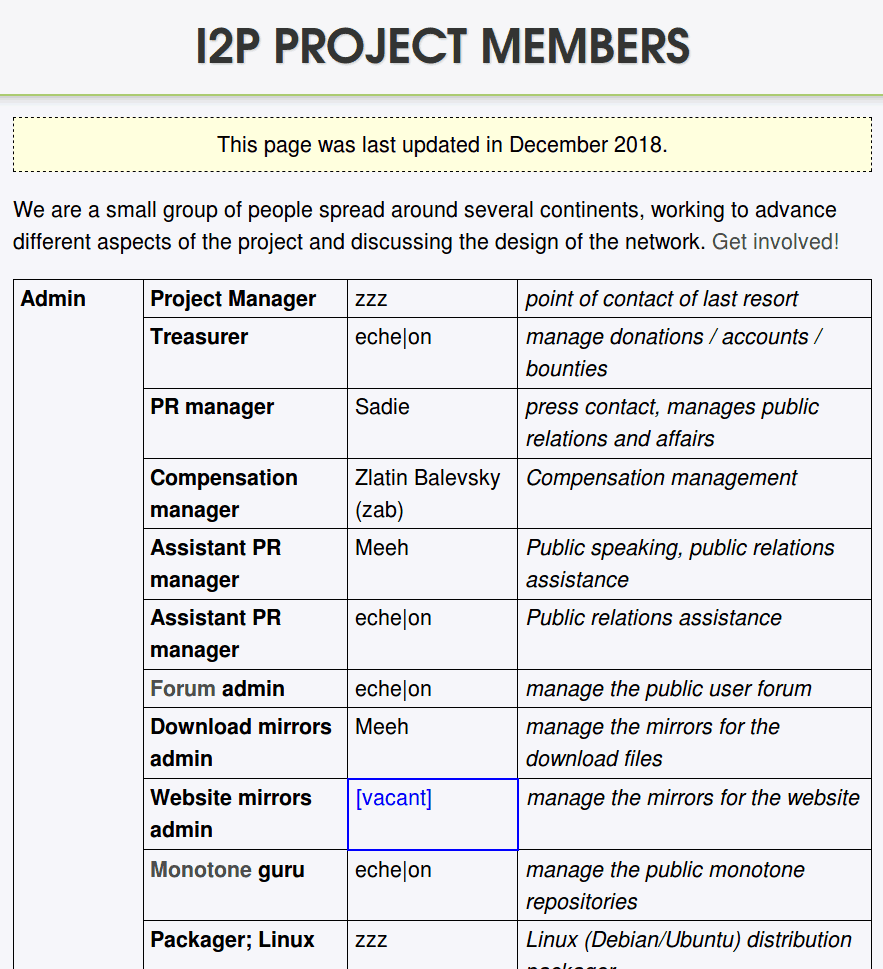
I2P Project Member List
You can see the most up-to-date list on the I2P Project Members page.
The distributed, mostly volunteer, and partially anonymous nature of the team has advantages and disadvantages. On the one hand, there isn’t some corporation or university to drive the project forward and be held responsible if something goes wrong. And, as far as we can tell, there are no big financial backers.
On the other hand, this makes it a lot harder to put pressure on the team. Who would you lean on to do something underhanded like put a backdoor into the code?
Add the fact that the I2P code is FOSS (Free and Open Source Software). With coders all around the world reviewing the code and looking for bugs or intentionally-inserted weaknesses, I2P is surely safer to use than most commercial software.
I2P is a network layer that runs on the existing Clearnet infrastructure. It provides layer 3 (network layer) functions, as defined in the OSI computer networking model. This means it handles routing of message packets and can handle message packets from any apps that connect to it. In other words, I2P can provide anonymous connections for other applications.

How does I2P work?
I2P runs on the computers of tens of thousands of users worldwide. Each such user runs the I2P Router on their computer, and provides encrypted, one-way connections to and from other users. The distributed, peer-to-peer structure of I2P makes it robust and difficult to attack.
I2P functions as a kind of Internet with the Internet. Anonymous hidden sites (called eepsites) and services exist that are only accessible to people using I2P. It is assumed that users will stay within the I2P network, rather than use I2P as an anonymous way to interact with the Clearnet.
Does I2P provide perfect anonymity?
There is no such thing as “perfect anonymity.” Instead, you should look at anonymity as more of a spectrum. As the designers of I2P put it, your level of anonymity is:
“How hard it is for someone to find out the information you don’t want them to know?”
Every anonymity system has strengths and weaknesses. Here are a few of the factors that affect how hard it is for someone to find out the information you don’t want them to know:
Getting your information requires someone hostile to you to defeat one of these factors and the willingness to expend the resources to do so. Whether that can or will happen depends on who that hostile someone is and what resources they are willing to use against you.
Which takes us to the concept of a threat model. Your threat model tells you who is likely to attack you, how they are likely to attack, and what they are likely to want to learn. For high-risk targets like whistleblowers, activists, and human rights activists, incorrectly modeling threats to their anonymity could cost their lives or freedom.

Does I2P provide perfect anonymity?
But for most of us, the threats are less urgent, and the value of capturing our information isn’t worth the expenditure of huge resources. Any system that provides any level of anonymity will protect us from most of the threats we are likely to see used against us.
Without getting into the technicalities of threat modeling, I2P provides at least some protection against the following threats:
How I2P Works to Protect Your Anonymity
To defend your anonymity against threats like these, each I2P user runs an I2P Router on their computer. This router makes some temporary, encrypted, one-way connections with other I2P Routers. All messages passing along these connections are protected by a cryptographic method known as garlic encryption.
Messages from your computer pass through Outbound Tunnels to other routers and are received through Inbound Tunnels of other routers.

How does I2P Work to Protect your Anonymity?
The lengths of the Inbound and Outbound Tunnels vary depending on the requirements of the user of the computer that created the tunnel.
The starting point of a tunnel is called the Inbound Gateway or Outbound Gateway. The final router in a tunnel is called the Inbound Endpoint or the Outbound Endpoint. Tunnel length is specified in “hops” and goes like this:
The length of each user’s Inbound and Outbound Tunnels is under their control. This allows users to balance anonymity, latency, throughput, and reliability as best serve their own needs. Tunnels with more hops provide greater anonymity, but result in reduced reliability and throughput, while increasing latency.
Note, however, that a user has control only over the length of his or her own tunnels. The owner of the destination controls the length of those tunnels. This means that the characteristics of the total connection between two users of I2P can vary greatly.
To find other users of I2P, you can consult the fully-distributed I2P network database. This lets you find the Inbound Tunnels of others using I2P. I2P supports both UDP and TCP messaging.
Users on the I2P Network?
Among other things, this means that once you connect to I2P, you can use a normal web browser to view eepsites and other resources. The I2PTunnel service allows users to create and host an anonymous eepsite using a standard web server. I2PTunnel also makes it possible to create an anonymous IRC network.
Another feature of this design is the ability to support streaming apps. An app called I2PSnark allows you to stream videos and other content across the I2P network using the BitTorrent protocol.
Now that you’ve got a good sense of what I2P is all about, let’s take a look at how I2P compares with two other privacy-oriented technologies: Tor and VPNs.
I2P and Tor have many similarities. They’re both anonymity services that rely on volunteer-run servers. But they have several key differences that make them suitable for different uses. The following quick summary of Tor will make discussing the differences easier.
Tor is an anonymity system with millions of users worldwide. It uses a network of volunteer-run servers to pass a message between your computer and a resource on the Internet. The message is encrypted and passes through three randomly selected servers using encrypted tunnels.

 Tor Browser
Tor Browser
Tor protects each piece of the message in three layers of encryption, a technique called “onion routing.” One layer of encryption gets stripped off at each server along the path, and the message exits the Tor network in its original (pre-encryption) state.
Tor is designed so that your ISP and anyone watching your computer’s connection to the Internet cannot read your message. They can only see that you are connected to Tor. No node (server) in the Tor network can see all the information it would need to identify you and tie you to a specific date.
The first node in the Tor network (the Guard Server) can see that a message is coming from your specific IP address, and where it is supposed to send the message next. But it cannot read the message.
The second node (the Middle Server) knows the first node sent the message to it, and that it needs to pass it along to the third node. But it can’t read the message, and it doesn’t know what IP address the message originally came from.
The third node (the Exit Relay) knows the second node sent the message to it. And, because it strips off the third layer of encryption, the third node knows what the message says. But it doesn’t know which IP address the message came from, so can’t associate the message with you. To further protect you, the Exit Relay aggregates data from multiple users and sends it out to the Clearnet all at the same time.
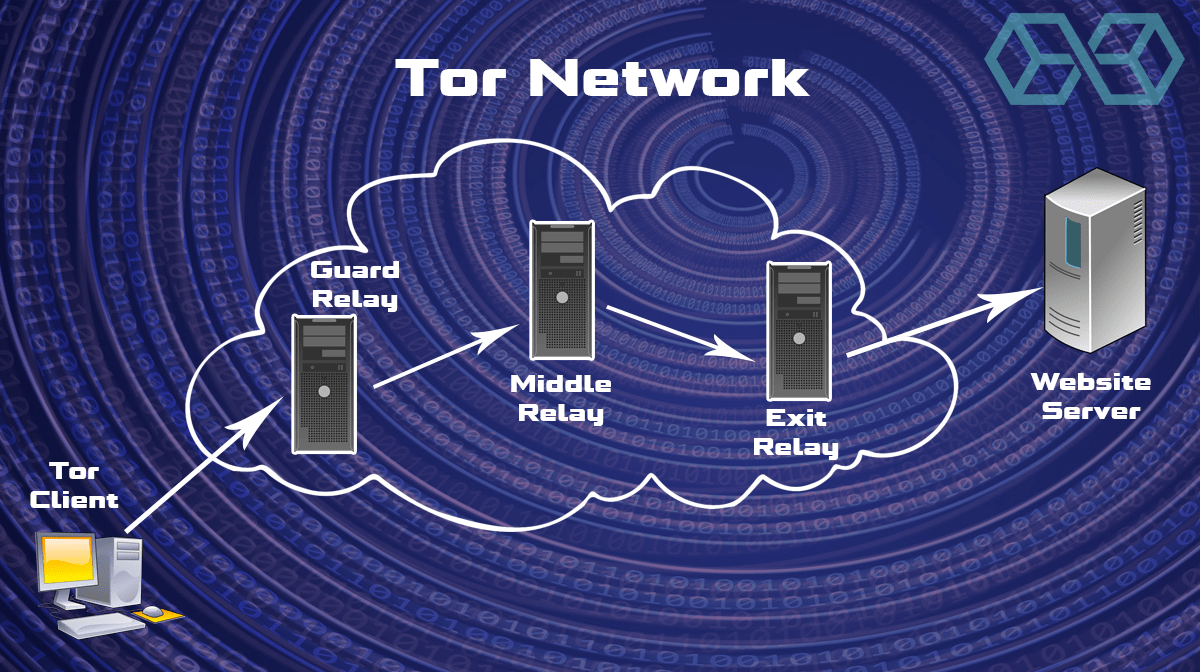
Tor Network Diagram
To boost performance, Tor configures several users to follow the same path through the network. Approximately every 10 minutes Tor changes the route that your data follows through the network.
Tor was designed for anonymous browsing on the Clearnet but does support hidden services, known as Onion Services. Statistics about the use of Tor are available at Tor Metrics.
Tor relies on a set of trusted Directory Servers that maintain lists of the available Relays. The addresses of these servers are included in the Tor installation, although you have the option to configure Tor to use different Directory Servers if you wish. I2P uses a distributed network database instead of trusted Directory Servers. The I2P approach is more secure since there are no fixed points (the Directory Servers) to attack.
Tor uses two-way encrypted connections between each Relay, while I2P uses one-way connections between every server in its tunnels. The I2P approach means that an attacker needs to compromise twice as many nodes in I2P as it does in Tor to get the same amount of information. But while Tor always uses three Relays to cross its network, with I2P the number of hops between two points in I2P can vary greatly.
TOR vs I2P
Accessing I2P’s eepsite hidden services is generally faster than accessing Tor’s Onion (hidden) Services.
Tor is a much larger and more mature network that has significant funding and has already addressed some of the scalability issues that I2P hasn’t yet experienced.
While both Tor and I2P provide access to the Clearnet as well as hidden services, their emphasis is the opposite. That is, Tor is primarily for accessing the Clearnet anonymously and secondarily for accessing the hidden Onion Services. I2P is primarily for accessing hidden services and transferring messages anonymously, with Clearnet access secondary.
For a much more detailed comparison of I2P with Tor, including a guide to their differing terminology, visit this I2P Compared to Tor page.
I2P and VPNs (Virtual Private Networks) are significantly different. However, VPNs are by far the most popular privacy-protection services used on the Internet today. While we don’t have exact numbers, reports show that there are probably more than 400 million VPN services users worldwide.
VPNs work by creating an encrypted tunnel between your computer and one of the VPN’s servers. Instead of message passing directly between your computer and some Internet resource, the VPN server passes messages to and from the resource.

How does VPN Work?
As far as the resource can tell, the message you send to it comes from the VPN server, and not from your IP address. This provides you with privacy, since neither your ISP, a spy monitoring your Internet connection, nor the resource can tell who you are.
However, a VPN doesn’t provide anonymity. This is because the VPN does potentially have the information to associate your message with your IP address. The best VPN services are more trustworthy than most ISPs when it comes to protecting personal data like your IP address. But you still need to trust your VPN to protect you. We recommend expressvpn or nordvpn for their strong data privacy practices.
VPNs are designed for fast, efficient private browsing of the Clearnet, while I2P is weakest at accessing the Clearnet.
VPN technology is much more mature than I2P, with hundreds of VPN service providers, and competition for billions of dollars of revenue driving their development.
As you will see, I2P is not really designed for the regular computer user. Configuring your web browser to work with I2P can be complicated. Installing most VPNs takes just a few moments and no specialized computer skills.
VPN vs I2P
Because I2P is a peer-to-peer network, any particular I2P resource is only available when the computer hosting that resource is online. VPN services typically include hundreds or thousands of servers that are online 24/7, minimizing the chances that your VPN connection will be unavailable.
Because the number of hops between points in I2P can vary greatly, the characteristics of the connection can also vary greatly. A VPN connection will always have one VPN server between your computer and the Clearnet.
How do you get access to I2P?
Getting I2P up and running on your computer is more complicated than installing the typical word processor or game. In general, you will need to do the following:
Let’s look at each of these steps in more detail.

Java
This one is pretty simple. Go to the ‘How Do I Install Java?’ page and follow the directions for your OS.
If you are concerned about anonymity, it would be better to do this on a computer running a version of Linux.
Linux versions are generally considered to be more secure than Windows or MacOS.
Once you have the latest version of Java installed, go to the I2P Download Page and download the I2P version for your OS. This page also includes instructions on how to launch I2P once it is downloaded and installed properly.
I2P Download Page
Use the SHA256 Signature listed for your OS to confirm that the download has not been corrupted or hacked.
Note: If you need instructions on how to verify a download using a SHA256 Signature, try this page.
Once you have a clean download, install I2P using the standard procedures for your OS.
Use the instructions that appeared on the download page to launch I2P. Depending on your OS, you may see a Console Window with additional instructions. The following figure shows the first step of configuring I2P in the Console Window of one of our test machines running Windows 7.
I2P Router Console
Once you configure I2P using the instructions for your OS, you need to configure your web browser to connect to I2P.
Configure Your Web Browser for I2P
This step could be tricky. The documentation for specific browsers on the I2P website is out of date. However, you should be able to get your browser set up by following the Firefox configuration instructions on the I2P Browser Configuration page.
Which browser should you use?
We used the latest version of Firefox (65.0.2) on our Windows 7 test machine and the instructions worked fine. Firefox has a better reputation for privacy then do Google Chrome or either of the Microsoft browsers.
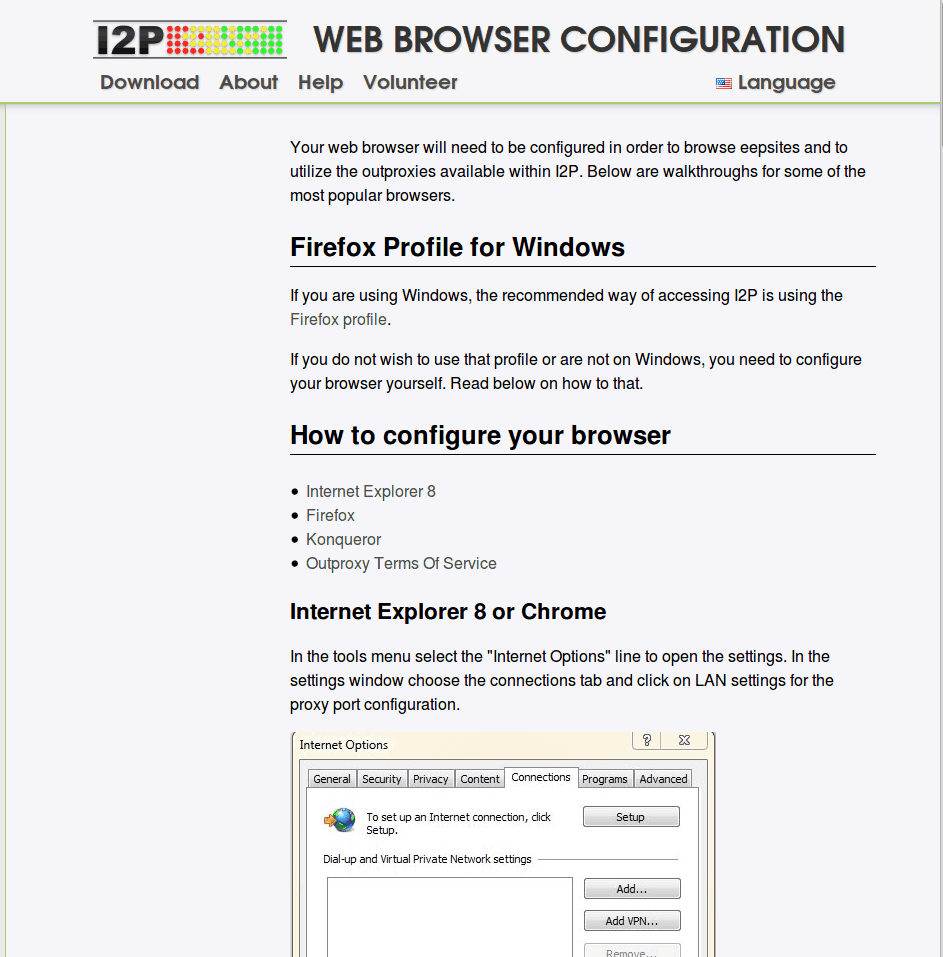
I2P Web Browser Configuration
Once you complete the process, you can launch the I2P Router Console and it will appear in your browser. After the browser has a few minutes to set up some tunnels, you should see something like this:
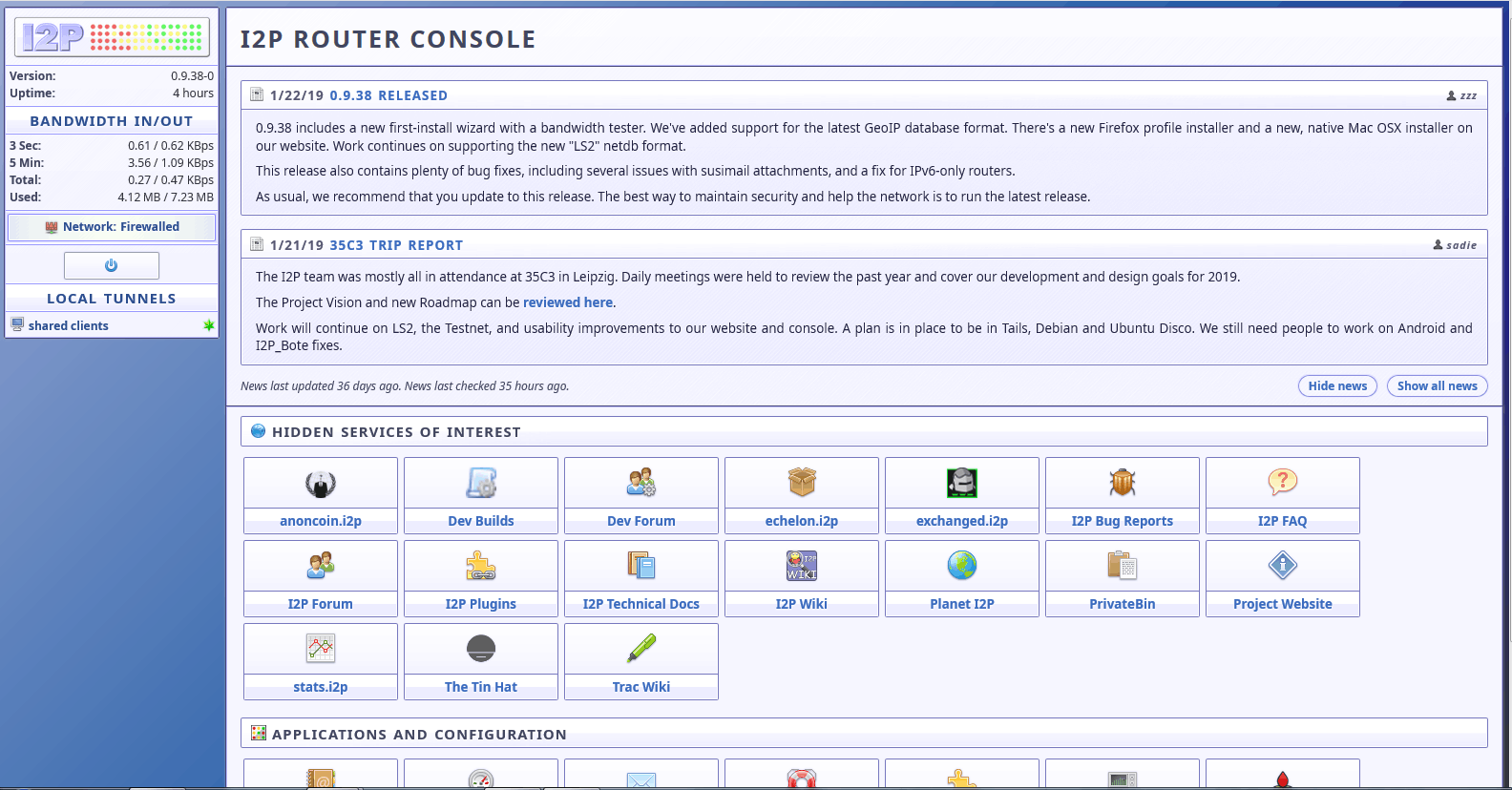
I2P Router Console
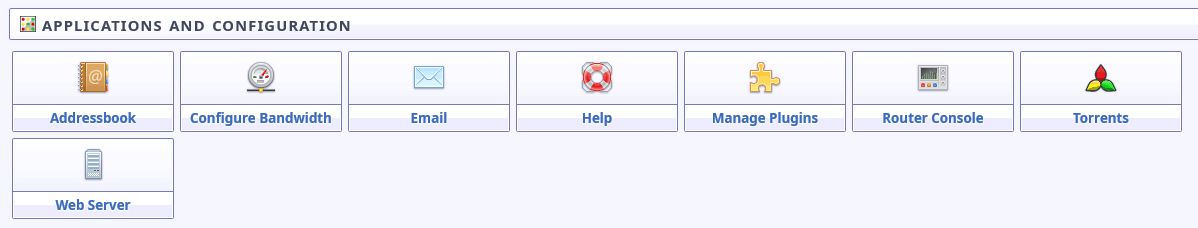
As you can see, from here you will have access to several interesting hidden services (eepsites). You’ll also have access to a collection of applications and configuration options like those shown below:
I2P Applications and Configuration
You’ll want to check out the applications/services that live behind some of these links. In particular:
The Addressbook automatically keeps track of the I2P resources you are subscribed to.
I2P Mail is a hidden email service that can communicate both with accounts inside I2P and outside on the Clearnet. This service has been available to the I2P community since 2004. For more information, check out the Postman HQ page.
This is the place to go if you want to understand everything you see on the I2P Router window.
This is where you go to use I2PSnark for streaming content. For help in using this service, visit this Anonymous Torrenting with I2PSnark page.
This is where you download the files and find the configuration instructions for creating your own eepsite. You can run your eepsite on the server here, or configure a traditional web server to connect to I2P through I2PTunnel.
Other Apps that Run on I2P
Beyond those listed above I2P supports other types of apps. Here are some of those types along with some specific examples of each type:
I2P Messenger was a standard IM app. Although it is no longer supported, the code is still available for download.
Other chat apps such as JIRCII, WeeChat, and HexChat use the IRC protocol and can run on I2P using I2PTunnel.
In addition to the bundled I2PSnark app, the Transmission BitTorrent client and opentracker BitTorrent tracker are available.
You can find an extensive list of additional applications on the I2P Supported Applications page. Unfortunately, many of the services listed here are no longer supported. If you want to go beyond the small set of bundled apps you should be prepared to do a lot of digging and to hit a lot of dead ends.
Because I2P provides for anonymous communications across the Internet, it seems like an ideal tool for anonymous cryptocurrencies. A couple of years ago, there was talk that Monero would use the I2P network as part of its anonymity system. As one of the top Privacy Coins, this would have boosted the number of I2P users, greatly increasing the anonymity of I2P.
But instead of connecting Monero directly to I2P, the Monero team decided to develop Kovri, “a free, decentralized, network anonymity technology” that is compatible with I2P. According to the Kovri FAQ, this technology is still in Alpha stage and is not used for Monero transactions.
In this article, we have looked at how I2P (Invisible Internet Project) works and how it compares against a VPN and Tor Browser as a privacy tool. We’ve also provided a step-by-step guide which shows you how to connect to I2P and start using it.
We hope you found this I2P guide to be very informative.


0 Comments